|
|
|
|
|
The Teach Cyber Byte
In this week's Byte, we define the term "Advanced Persistent Threat" (APT), identify some APT groups from around the world, and look at a recent example of a suspected APT attack. Feel free to forward and share! (Please note: if you forward this to someone else and they click "unsubscribe", you may be unsubscribed from the mailing list.)
|
|
|
|
|
|
"Advanced Persistent Threat" (APT)
|
|
|
|
APTs are sophisticated, systematic, targeted cyber-attacks which go undetected for long periods of time. APT actors infiltrate networks and lurk in these networks, stealing high value information or compromising infrastructure. Once inside of a network, they look for ways or use tools to maintain persistent access. On average, APT actors are inside networks and systems for one year (with multi-year durations up to five years of entrenchment reported) before being discovered. For many cybersecurity professionals, APTs are what keep them up at night!
|
|
|
|
|
|
|
APTs attack high-value targets, such as intellectual property or trade secrets (i.e., "Proprietary Information"); infrastructure systems; or political targets.
|
|
APTs are carried out by APT groups. These groups are made up of highly skilled adversaries. They are not random attackers. They have a predetermined objective, and they are adaptable and willing to spend months or years on an attack to achieve their objective. APT groups are typically sponsored by nation-states. A country (nation-state) supports an APT group that acts on behalf of that nation-state’s interests. Sometimes, APT groups are associated with a country’s military or intelligence operations.
|
APTs are usually motivated by economic or political reasons. For example, a nation-state might steal trade secrets from a foreign company to gain an economic advantage in a specific industry; or a nation-state might attempt to interfere with another country’s elections (this may be done to sow distrust in the victim country’s political process, or to elect a candidate who is more favorable to the attacking nation-state). In other instances, the objective of an APT is to affect critical infrastructure such as power or water. Imagine a scenario in which a foreign APT group takes out chunks of the U.S. electrical grid – businesses, hospitals, communications would all come to a grinding halt… How serious would the consequences be?
|
APTs are notoriously hard to trace. Part of understanding and tracking APTs comes through threat intelligence. Threat intelligence is, in the most general sense, knowledge about adversaries used to better understand past, current, and future threats to an organization. Threat intelligence comes from information collected from a variety sources. Once collected, this information is checked for reliability, processed, examined to determine whether the threat is real, then analyzed. Threat intelligence is a continuous cycle.
|
|
Through threat intelligence, APTs have been identified and attributed[1] to countries all around the world. Let’s look at a few APT groups...
|
|
|
|
|
|
|
|
APT-1
A seminal report covering APT-1 was released by Mandiant in 2013[2]. APT-1 is attributed[1] to China's 2nd Bureau of the People's Liberation Army (PLA) General Staff Department's (GSD) 3rd Department (Military Cover Designator 61398). In 2014, there was a U.S. Department of Justice indictment of five 61398 officers on charges of stealing confidential business information and intellectual property from U.S. commercial firms and of planting malware on the firms’ computers.
|
APT-29
More recently, APT-29 has targeted various organizations involved with COVID-19 vaccine development in Canada, the United States, and the United Kingdom. APT-29 (also known as “the Dukes” or “Cozy Bear”) is a cyber espionage group which is likely[1] part of the Russian intelligence services. A report was issued by the U.K.’s National Cyber Security Centre (NCSC) with agencies from Canada and the U.S. (NSA and CISA) contributing to the effort[3].
|
In September, 2020, FBI Director Christopher Wray told the House Homeland Security Committee that foreign hackers searching for ways to steal information and research about COVID-19 vaccines are an on-going threat, including threats from China, Russia, and Iran[4].
|
Stuxnet
|
APTs are not only perpetrated against the U.S. The U.S. sponsors its own APTs to advance U.S. interests. One example of this is Stuxnet (though there is some debate about whether Stuxnet truly classifies as an APT). Stuxnet was a computer virus developed jointly between U.S. and Israeli agencies. In 2010, Stuxnet was deployed against Iran and reportedly ruined almost 20 percent of Iran’s nuclear centrifuges. This slowed Iran’s ability to produce nuclear weapons. More recently, in July 2020, a nuclear site in Iran exploded. Iran blamed this explosion on a cyber-attack. It’s speculated that the explosion was caused by a new variant of Stuxnet.
|
|
|
|
|
|
|
WORD OF THE WEEK IN ACTION
|
|
|
APT groups are highly skilled, adaptable, and usually backed with significant resources. Attacks by APT groups can be serious, sophisticated, and far-reaching. Let's look at an example of a suspected APT attack...
|
|

|
|
|
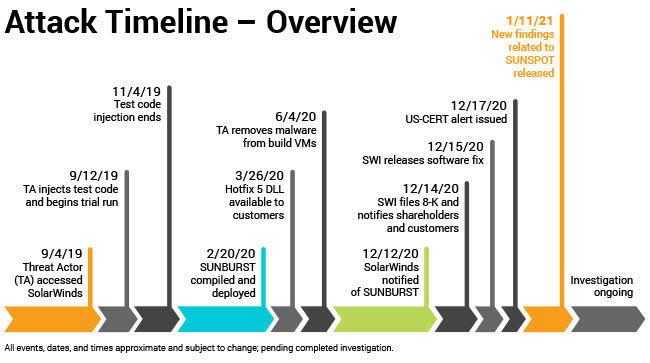
In December of 2020, news broke that there had been a complex supply chain attack against SolarWinds, Inc (an American company which develops network monitoring software for businesses)[5]. The attack may have resulted in malicious code being sent out to up to 18,000 SolarWinds customers, including U.S. federal agencies and Fortune 500 companies. Over 425 firms on the Fortune 500, all branches of the U.S. military, the Centers for Disease Control and Prevention, and more were affected (including AT&T, MasterCard, the Gates Foundation, and Comcast)[6]. This attack consists of highly sophisticated and complex attack designed to circumvent threat detection[7]. Key points of the attack:
|
- Replaced one of the software (C#) files that is compiled and combined in the process to build new versions of software updates[5].
- Code for a backdoor was inserted in this C# file. The backdoor is capable of transferring files, disabling services and rebooting machines. This likely means more upcoming disclosures of multiple, potentially massive, data breaches (see the Teach Cyber Byte | 11/04/2020 for more information about the term "data breach") as the scope and impact of the attack is assessed[5].
- This sophisticated code was designed to avoid detection, and creators had intimate knowledge of the software development environment[5].
- The altered (hacked) updates came from the company, so they were trusted and installed on roughly 18,000 networks. It is already reported that they have broken into email accounts and the affected networks[5].
|
|
|
|
|
It appears the attack was intended for espionage [6]. While the perpetrators have not been identified, the fact that the attack targeted the U.S. government, military, and tech firms points to one or more APT groups.
|
|
|
|
|
|
|
|
This lesson introduces the definition of and examples of Advanced Persistent Threats. Through a discovery-based inquiry, students research APT attacks in the context of vulnerabilities exploited, the intent of the attack, and the attackers’ capabilities and resources.
|
APT groups are a prime example of how nation-states wield cyber to advance their own interests. Cyber is revolutionizing international conflict. How is conflict changing? Are our laws and regulations keeping pace? To explore these questions, check out Unit 8, Lesson 2.
|
|
In Unit 8, Lesson 2, students examine instruments of national power and define cyber as an instrument of power. Then, students choose from one of two research projects: Cyber Weapons and The Changing Nature of War; or Technopower/Technowar.
|
|
|
|
|
|
[1] Terms such as “attributed” and “likely” describe suspected countries behind these APT groups. Adversaries don’t usually leave a name and address for researchers and intelligence gatherers. Instead, clues from the tactics, tools / techniques and procedures (TTPs) are used to build a profile of an APT.
|
|
|
|

|
|
|
|
|